News & Blogs
-
.png)
Why Every Business Needs a Comprehensive Backup and Recovery Strategy
Every business needs a strong backup and recovery strategy to protect data, minimise downtime, meet compliance, and maintain customer trust. Explore what a comprehensive plan should include, why it matters, and how LoughTec can help keep your busines... -

16 Billion Passwords Leaked in Largest-Ever Data Breach !
16 Billion Passwords Leaked in Largest-Ever Data Breach !Researchers have confirmed what may be the largest password breach in history, with more than 16 billion login credentials, including usernames and passwords, leaked online.... -

From a Cyberattack to Insolvency
Fasana, a historic paper napkin manufacturer founded in 1919, has filed for insolvency after a severe ransomware attack brought its operations to a standstill.... -

OWASP Top 10 Common Vulnerabilities
Discover the OWASP Top 10 web application vulnerabilities every business should understand. Learn what they mean, see real-world examples, and explore practical steps to fix themhelping you build more secure software and reduce your risk of cyber thr... -

What is a Security Operations Centre & Why Your Business Needs One
Discover why a Security Operations Centre (SOC) is vital for modern businesses of all sizes. From 24/7 threat monitoring to expert response, compliance support, and cost-effective protection, learn how a SOC helps defend your business in todays evolv... -
.png)
Big Email Changes: DMARC and DKIM Enforcement
Learn how DMARC and DKIM work together to protect your email systems, meet new compliance requirements from Microsoft, Google, and Yahoo, and reduce the risk of phishing, spoofing, and delivery issues.... -
.png)
What is an Insider threat?
Protect your business from insider threatswhether malicious or unintentional. Learn how access controls, monitoring tools, and security awareness training can help mitigate risks. Discover key strategies to safeguard sensitive data and maintain a str... -
.png)
Cybersecurity Hygiene Best Practices Checklist
Protecting your business from cyber threats starts with strong cyber hygiene. From managing assets and securing networks to enforcing access controls and training employees, every layer of security plays a crucial role. Learn how to implement best pr... -
.png)
What is the Difference Between 2FA and MFA?
Discover the key differences between Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA), their pros and cons, and when to use each for optimal security. Explore real-world case studies showing how businesses, banks, and government ... -
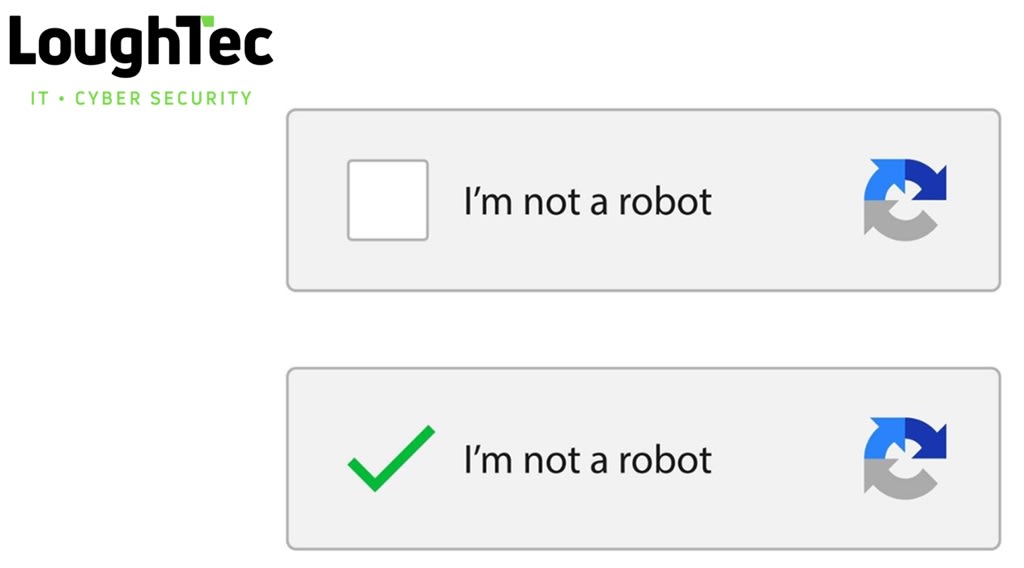
How do I know if my CAPTCHA is real ?
Serious malware is being downloaded resulting in data breaches and cyberattacks from cybercrimals loading fake Captcha methododlogies !... -
.png)
The Cyber Security Threats Lurking in Your Web Browser
Web browsers are essential for everyday use but can also expose you to cyber threats like phishing, session hijacking, and data theft. Learn about key security risks, how attackers exploit browser vulnerabilities, and best practices to protect your s... -
.png)
Ransomware Attacks: What to Do and What to Avoid
In the event of a ransomware attack, quick and calculated actions are vital to minimize damage. This guide offers essential steps on what to do and what to avoid during a ransomware attack, as well as effective prevention tips to safeguard your busin... -

What is The Difference Between Passwords and Passkeys
Discover the key differences between passwords and passkeys in our latest blog.Learn how these two authentication methods work, their strengths and weaknesses, and why passkeys are emerging as a more secure and user-friendly alternative... -
.png)
The A-Z Breakdown of IT and Cyber Security Abbreviations
The IT and cyber security world, like a lot of industries, is full of abbreviations. In this blog, we provide an A-Z breakdown of some widely used abbreviations to help explain some of the widely used terms.... -
.png)
Is My Business A Target for Cyber Criminals?
Frequently people ask us at LoughTec, why would someone hack me, I am only a small or medium sized business?... -

QUANTUM COMPUTING
Googles new quantum computing chip WILLOW has delivered almost incomprehensible performance !... -

Krispy Kreme Hacked
Krispy Kreme has reported a cybersecurity breach that disrupted its online operations in certain parts of the United States. The company cautioned that this incident could have a significant impact on its business.... -

BT Group Cyber Attack
BT Group has confirmed it is addressing an attempted cyberattack on one of its legacy business units following claims by the Black Basta ransomware group.... -
.png)
DELOITTE UK HACKED ?
Deloitte UK, a big 4 accounting firm who provide audit and assurance, tax, consulting and risk and financial advisory services to a broad cross-section of the largest corporations and governmental agencies have apparently been hacked with a large 1TB... -
.png)
What is Malware?
Discover the key to understanding and defending against malware. This blog breaks down 12 types of malware, including viruses, ransomware, spyware, and cryptojacking, explaining how they operate, their potential impacts, and the steps you can take to... -
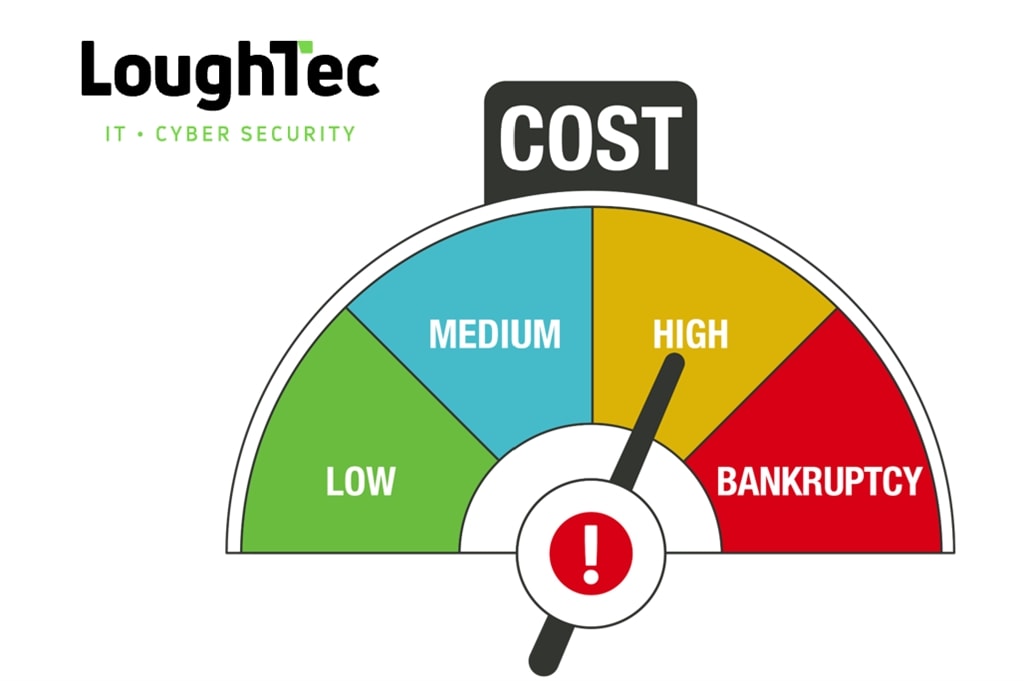
The cost of Cyberattacks in the UK
Cyberattacks cost U.K. businesses approximately 44 billion in lost revenue over the past five years...





